#wireless modems
Explore tagged Tumblr posts
Text
Make Daily Tasks Easy with Wireless Modems in Australia
In today's busy world where digital is the main priority. We are more inclined towards gaming, streaming, and online activities doing all the work remotely. In all this having a reliable, fast, internet connection has become a necessity. This can only be achieved if we have an Internet connection that gives us high speed. In order to get a better higher speed, one needs to have a wireless modem in Australia.

What is the use of wireless routers in Australia?
It is a kind of a device that can be connected with a router or may be combined to a modem router unit which is a type of device for connecting your home network or office to the Internet service provider. The best modem router in Australia is different from the old age style of wired setups. Instead, it is wireless and helps in connecting to the Internet through Wi-Fi and it's the requirement for any kind of ethernet Cables.
Top features to find the Best Wifi Router in Australia:
1. Easy to Connect with ISP and Internet Time
It is essential for you to make sure that the Wireless Modem in Australia must be compatible with the current connection type, no matter whether you are using ADSL, NBN 4G or 5G. Or, you can simply go for NBN approved modems. If in case you want to switch from ISP or want to upgrade your plan.
2. Tri-Band WiFi or Dual Band
There are different modern modems that easily support 5G, Hertz and 2.4. Frequency bands. There are dual bands also, but Tri bands make it easy to connect with five GHz bands and are highly suitable for homes or where you want to use multiple devices.
3. Wi-Fi Standards
At present, Wi-Fi 6 is the best wifi router in Australia with an ongoing standard. It gives you faster speed., enhanced security. Superior performance. 6 E you can actually get to extend your bandwidth. But it can be. Supported for only newer devices.
4. USB Connectivity and LAN Ports
If you are a gaming person, or use desktop pieces or have a smart TV at your home, then there are chances you might require multiple GB Ethernet ports. To have a high speed connection you need to have USB ports that are handy for network attached storage.
5. Enhanced Security Features
Go for WPA3 encryption, guest networks, parent roles and automatic firmware updates. In today's world, cyber security has become necessary, most importantly if you are working from home.
The Last Lines
Getting a wireless modem in Australia surpasses the idea of choosing the famous brands. Moreover, choosing the best modem router in Australia is more like ensuring that it can be easily compatible with your current Internet type and supports your usage habits. Give your lifestyle a tech upgrade with a connectivity lifeline.
#Wireless Modems Australia#Wifi Routers Australia#Best Wifi Router Australia#Best Modem Router Australia
0 notes
Text
🚀 Big news! Apple has unveiled its first custom-designed C1 modem chip, marking a significant leap in wireless technology. Say goodbye to Qualcomm reliance and hello to improved connectivity and battery life! 🌐✨ #Apple #C1Modem #WirelessTechnology #iPhone16e
#Apple#battery life#C1 modem chip#chip design#iPhone 16e#Qualcomm#smartphone connectivity#wireless technology
0 notes
Text
Wireless Data Radio Modem Market Size - Industry Trends and Forecast to 2030
The Wireless Data Radio Modem Market is expected to grow from USD 594.4 Million in 2018 to USD 724.1 Million by 2023, at a CAGR of 4.03% between 2018 and 2023.
The growth of the wireless data radio modem market is driven by the growing demand for radio modems in agricultural drones and surveys, dominance of radio modems in SCADA and telemetry applications, and low operational costs and more power-efficiency of private radio networks using radio modems. Moreover, increase in the number of exemptions for the use of UAV drones in the commercial applications is the major opportunity for the growth of the market.
The major players in the wireless data radio modem market include SATEL OY (Finland), Motorola Solutions (US), Schneider Electric (France), Digi International (US), Pacific Crest (US), Advantech B+B SmartWorx (US), FreeWave Technologies (US), Cohda Wireless (Australia), Campbell Scientific (US), and Harris Corporation (US).
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=29689326
General-purpose wireless data radio modems expected to hold larger size of wireless data radio modem market between 2018 and 2023
The long life cycle of radio modems in the enterprise, due to dedicated spectrum and longer battery life, is expected to propel the growth of the general-purpose radio modem market during the forecast period. Moreover, the demand for radio modems is increasing as these modems require minimal infrastructure for facilitating communication and ensuring the delivery of data, in the form of voice and video, in the most cost-effective and reliable manner.
Wireless data radio modem market for long range to grow at higher CAGR between 2018 and 2023
The long-range wireless radio data modem for 910 MHz/2.4 GHz is designed with unmatched radio frequency (RF) performance and for extremely robust long-range frequency hopping. It is the most robust and cost-effective means of the industry for providing embedded long-range data communications between industrial serial communication devices.
Wireless data radio modem market in APAC to grow at highest CAGR between 2018 and 2023
This report segments the market into North America, Europe, Asia Pacific (APAC), and Rest of the World (RoW). The growth of the wireless data radio modem market in APAC is attributed to the increasing adoption of radio modems with the development of the transportation infrastructure, and mining and utilities industries in the region. The major countries in APAC such as India and China have started recognizing ITS as a crucial tool to solve social, economic, and environmental problems caused by traffic congestion, air pollution, and increased greenhouse gas emissions.
0 notes
Text
How to Dlink Router Setup Without Modem?
The problem might occur if you're utilising your router to build a private local network, increase the range of your Wi-Fi, or for some other particular reasons.

This thorough guide will show you how to configure your "D-Link router without a modem" so that it functions as a potent tool for local networking.
1. Determine Your Router's Capabilities
The first step is to see if this configuration is supported by your D-Link router. Not every router is made to function without a modem. For details on the router's capabilities, check the manual or go to the D-Link website. These routers are frequently referred to as "bridge mode" or "router mode."
2. Hardware Setup
It's time to begin the hardware installation once you've determined that your router is appropriate for this configuration.

Turn on the router by plugging it into an electrical outlet. Connect your computer to one of the LAN (Local Area Network) ports on the router using an Ethernet connection. The initial configuration requires this connected connection.
3. Access the Router's Web Interface
You must visit the router's web-based setup page in order to configure it. The default IP address of the router should be typed into the address bar of an open web browser on your computer. Common IP addresses for D-Link routers include 192.168.0.1 and 192.168.1.1. For the precise IP address, consult the user guide for your router.
4. Login to the Router
A username and password must be entered in order to access the router's settings. Try entering "admin" for both fields if you haven't modified the default values for these credentials. The login credentials should be changed for security reasons.
5. Internet Configuration
You will have to manually enter your Internet Service Provider (ISP) information into the router because you are configuring the router without a modem.
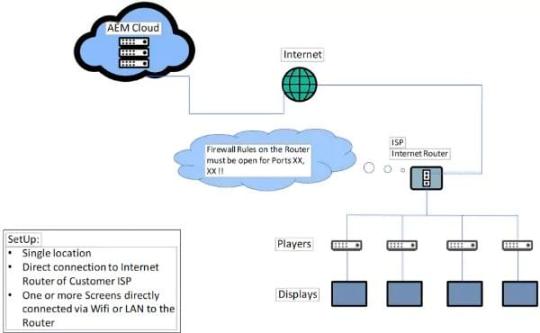
To get the relevant information, which normally includes the IP address, subnet mask, and DNS server details, get in touch with your ISP. Put these parameters in the router's configuration.
6. Local Network Settings
Adjust the router's local network settings as needed. You can enable the DHCP (Dynamic Host Configuration Protocol) server to automatically assign IP addresses to devices on your local network. Ensure that your router's DHCP server is activated.
7. Wireless Network Configuration
Set your SSID (Network Name) and password to configure your Wi-Fi network. For wireless device connections to your router, this is essential.
8. Security Measures
Put security measures in place to prevent unauthorised access to your network. Use WPA3 encryption on your Wi-Fi network and set a strong administrator password.

9. Testing Your Network
Test your network after configuring the router to make sure everything is working as it should. Check internet connectivity on a variety of devices connected to your Wi-Fi network, and make sure all settings are being used as intended.
Conclusion
For a number of networking requirements, setting up a "D-Link router without a modem" can be a workable alternative. This post has showed you how to set up a private local network, increase your Wi-Fi range, or experiment with various network setups. You may efficiently administer your network without a typical modem using the correct D-Link router and the instructions provided here, giving you flexibility and control over your network environment.
#how to setup a router without a modem#wifi router without modem#can you have a router without a modem#wireless router without modem#dlink modem setup
0 notes
Text

315MHz Transmitter Module: A Versatile Wireless Solution
In the realm of wireless communication, the 315MHz transmitter module stands out as a versatile and indispensable component. This article explores the significance of the 315MHz transmitter module, its functionalities, and the array of applications it serves in modern technology.
Understanding the 315MHz Transmitter Module
The 315MHz transmitter module is a compact electronic device designed to transmit data wirelessly using radio waves. This module is the singular solution for enabling efficient and reliable wireless communication across various sectors.
Applications of a 315MHz Transmitter Module
Remote Control: The 315MHz transmitter module finds widespread use in remote control systems, such as garage door openers, home automation, and even toy controllers. Its ability to transmit commands wirelessly simplifies everyday tasks.
Security Systems: Home and industrial security systems often rely on the 315MHz transmitter module to transmit signals from sensors and alarms to a central control unit. This ensures real-time monitoring and immediate responses to security incidents.
Wireless Sensors: In applications like tire pressure monitoring systems and health monitoring devices, the 315MHz transmitter module plays a crucial role. It allows these devices to wirelessly transmit data for analysis and action.
How the 315MHz Transmitter Module Operates
The operation of the 315MHz transmitter module is straightforward. It accepts electrical signals from a source, typically a sensor or microcontroller, and converts them into RF signals for wireless transmission. These RF signals are then broadcasted via an antenna to reach the intended receiver.
On the receiving end, an RF receiver module tuned to the same frequency captures and processes these RF signals, making the transmitted data available for further use.
Benefits of the 315MHz Transmitter Module
Extended Range: The 315MHz frequency offers an excellent balance between range and power consumption, making it suitable for applications that require communication over moderate distances.
Reliability: This transmitter module ensures reliable communication, even in environments with obstacles or interference.
Low Power Consumption: Many 315MHz transmitter modules are designed to operate efficiently with minimal power consumption, making them ideal for battery-operated devices.
Ease of Integration: Thanks to standardized protocols and interfaces, integrating the 315MHz transmitter module into various electronic systems is a straightforward process.
Conclusion
The 315MHz transmitter module is a singular solution for wireless communication needs. From enhancing the convenience of remote controls to ensuring the security of our homes and industries, this module is at the core of many essential technologies. As technology continues to evolve, the 315MHz transmitter module will remain a crucial component in our increasingly interconnected world.
For details, please click: https://www.nicerf.com/ask-modules/ask-transmitter-module-stx885.html
Or click: https://www.alibaba.com/product-detail/G-NiceRF-STX885-Small-size-with_1600934177861.html?spm=a2747.manage.0.0.52dc71d2eZn7o0
For consultation, please contact NiceRF (Email: [email protected])
#GPS#IOT#wireless#RF#LoRa#module#modem#transmitter#receiver#wireless module#lora module#rf transmitter and receiver#315mhz transmitter module
0 notes
Text
Wireless Data Radio Modem Market Analysis Forecast till 2032

Wireless Data Radio Modem Market size was valued at USD 527.87 Million in 2021 and is projected to reach USD 739.30 Million by 2030, growing at a CAGR of 3.82% from 2023 to 2030.
The competitive analysis of the Wireless Data Radio Modem Market offers a comprehensive examination of key market players. It encompasses detailed company profiles, insights into revenue distribution, innovations within their product portfolios, regional market presence, strategic development plans, pricing strategies, identified target markets, and immediate future initiatives of industry leaders. This section serves as a valuable resource for readers to understand the driving forces behind competition and what strategies can set them apart in capturing new target markets.
Market projections and forecasts are underpinned by extensive primary research, further validated through precise secondary research specific to the Wireless Data Radio Modem Market. Our research analysts have dedicated substantial time and effort to curate essential industry insights from key industry participants, including Original Equipment Manufacturers (OEMs), top-tier suppliers, distributors, and relevant government entities.
Receive the FREE Sample Report of Wireless Data Radio Modem Market Research Insights @ https://stringentdatalytics.com/sample-request/wireless-data-radio-modem-market/2639/
Market Segmentations:
Global Wireless Data Radio Modem Market: By Company • Adeunis • Atim Radiocommunications • Campbell Scientific • Cohda Wireless • Encom Wireless • Harris Corporation • Intuicom • Pro4 Wireless • Advantech B+B Smartworx • Freewave Technologies • Microhard Systems • Pacific Crest • Digi International • Woods & Douglas • Simrex Corporation • MotoRola Solutions • Satel OY • Arada Systems • Javad Gnss • Schneider Electric • GE Grid Solutions • Harxon Corporation • ABB Global Wireless Data Radio Modem Market: By Type • Short Range • Long Range Global Wireless Data Radio Modem Market: By Application • SCADA & Telemetry • Precision Farming • Transportation
Regional Analysis of Global Wireless Data Radio Modem Market
All the regional segmentation has been studied based on recent and future trends, and the market is forecasted throughout the prediction period. The countries covered in the regional analysis of the Global Wireless Data Radio Modem market report are U.S., Canada, and Mexico in North America, Germany, France, U.K., Russia, Italy, Spain, Turkey, Netherlands, Switzerland, Belgium, and Rest of Europe in Europe, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, China, Japan, India, South Korea, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), and Argentina, Brazil, and Rest of South America as part of South America.
Click to Purchase Wireless Data Radio Modem Market Research Report @ https://stringentdatalytics.com/purchase/wireless-data-radio-modem-market/2639/
Key Report Highlights:
Key Market Participants: The report delves into the major stakeholders in the market, encompassing market players, suppliers of raw materials and equipment, end-users, traders, distributors, and more.
Comprehensive Company Profiles: Detailed company profiles are provided, offering insights into various aspects including production capacity, pricing, revenue, costs, gross margin, sales volume, sales revenue, consumption patterns, growth rates, import-export dynamics, supply chains, future strategic plans, and technological advancements. This comprehensive analysis draws from a dataset spanning 12 years and includes forecasts.
Market Growth Drivers: The report extensively examines the factors contributing to market growth, with a specific focus on elucidating the diverse categories of end-users within the market.
Data Segmentation: The data and information are presented in a structured manner, allowing for easy access by market player, geographical region, product type, application, and more. Furthermore, the report can be tailored to accommodate specific research requirements.
SWOT Analysis: A SWOT analysis of the market is included, offering an insightful evaluation of its Strengths, Weaknesses, Opportunities, and Threats.
Expert Insights: Concluding the report, it features insights and opinions from industry experts, providing valuable perspectives on the market landscape.
Customization of the Report:
This report can be customized to meet the client’s requirements. Please connect with our sales team ([email protected]), who will ensure that you get a report that suits your needs. You can also get in touch with our executives on +1 346 666 6655 to share your research requirements.
Enquiry Before Buying @ https://stringentdatalytics.com/inquiry/wireless-data-radio-modem-market/2639/
About Stringent Datalytics
Stringent Datalytics offers both custom and syndicated market research reports. Custom market research reports are tailored to a specific client's needs and requirements. These reports provide unique insights into a particular industry or market segment and can help businesses make informed decisions about their strategies and operations.
Syndicated market research reports, on the other hand, are pre-existing reports that are available for purchase by multiple clients. These reports are often produced on a regular basis, such as annually or quarterly, and cover a broad range of industries and market segments. Syndicated reports provide clients with insights into industry trends, market sizes, and competitive landscapes. By offering both custom and syndicated reports, Stringent Datalytics can provide clients with a range of market research solutions that can be customized to their specific needs.
Reach US
Stringent Datalytics
+1 346 666 6655
Social Channels:
Linkedin | Facebook | Twitter | YouTube
0 notes
Text
youtube
TP-Link Deco AX3000 WiFi 6 Mesh System(Deco X55) - Covers up to 6500 Sq.Ft. , Replaces Wireless Router and Extender, 3 Gigabit ports per unit, supports Ethernet Backhaul (3-pack)
Note You may find some differences at the item specs that is because the same item specs are not available at all countries, but we are keen to put the most similar item buy link
#bestmostreliable#best_most_reliable#tplink#wifi#router#internet#modem#dlink#tecnologia#g#hp#epson#wireless#networking#acer#mikrotik#hikvision#network#technology#komputer#samsung#ubiquiti#a#printer#tplinkrouter#venezuela#cctv#cisco#xiaomi#canon
1 note
·
View note
Note
Concept: the Staff of Forbidden Spinjitzu doesn't whisper to Zane. Instead, its "whispers" take the form of popups along his HUD disguised as alerts or warnings. Things like "If you put me down now, your friends will never find you. [OK]” or “Killing these prisoners villagers will increase Vex’s approval and reinforce your reign. Proceed? [Y/N]”
(I like this particular flavor because it really leans into Zane's robotic nature: he can ignore whispers by turning off his auditory sensors or filtering noise, but he can't ignore system alerts.)
Also, the following scene has lived rent-free in my brain ever since I came up with the concept. (Italics are Zane's default OS. Everything else is the Staff.)
>IF YOU ARE GOING TO DESTROY ME, "ZANE" -Move File:"NeverrealmMemories" to Core Memory Functions-WARNING: Attempting to delete, move, or suppress File"NeverrealmMemories" after moving will cause total system failure. Proceed with move anyway? >[YES] -File transferred. -Permanently remove fatal combat safeguards? >[YES] -Safeguards removed. >THEN I WILL MAKE SURE YOU CAN NEVER FORGET WHAT YOU DID, SYSID:ICEEMPEROR
-Connection Terminated.
(I have a few more Ideas for the "Scroll Corruption looks like Computer Alert messages to Zane" idea-ones that really lean into Zanes Nindroid nature, as well as the tech-y appearance of the Dark Ice.) -The Staff did a lot more than just send alert messages: it slowly wormed its way into Zane's code like a computer virus, tweaking a few things. It took great care to remove Zane's combat safeguards, eventually deleting them entirely and ensuing he defaulted to lethal force. It never removed his core directive of "Protecting those who cannot protect themselves" since that was vital to his systems running, but it did reinterpret said directive as "Protect Dark Ice Network and everything connected to it, for it is fragile and cannot protect itself from outsiders". (It also couldn't delete his morality subroutines without causing a crash, so it instead made them a much lower priority and shoved them to the back of his digital mind.) -After 60+ years of being in the grasp of a mechanical being, the Staff now exclusively speaks in the manner of a computer, and cannot adapt to organic minds the way it used to. (The other Staff is not like this, as it's still attuned to organic brains.) -You know those Sci-Fi stories where people are plugged into computers and know every part of the ship/city simultaneously, and can send most of their awareness into certain parts of the network while still being aware of other locations? That's what's going on with the Never Realm during the Ice Emperor's Reign, with the Ice Emperor as the central guiding consciousness/core CPU of the Dark Ice Network. As such, he's not actually sleeping-rather, the Ice Emperor is always monitoring his domain through his Ice and leaving just enough of his consciousness in his body to be able to call the rest of himself back in case he's threatened. (The Staff is a combination of a computer virus and a wireless modem: it is corrupting, but it's also the main point of connection for the Dark Ice Network.) -Since the Ice Emperor can't recharge his power on his own in his current state, the Staff had to step in, tweaking the Dark Ice to drain the vitality of those imprisoned within. (You know wireless phone chargers, or Nikolai Tesla's idea to get electric power from the atmosphere? Similar concept, except with the power source being frozen people and the transmitter being Evil Magic Ice.) -Boreal is the Titanium Dragon, corrupted by the Staff's presence. It too is part of the Dark Ice Network, and serves as Ice Emperor's eyes and ears whenever the Dark Ice can't reach. (If the Ice network used computer program language, Boreal would be known as "Obj_DarkIceTitaniumDrake".) Killing Boreal caused a massive jolt to the Dark Ice Network that destabilized the Scroll's influence, and allowed an opening for Zane's Memory Defragmentation program to kick in. (It had started when Lloyd arrived in the throne room, but the Scroll had diverted that to a minor priority and was actively hiding that set of files until the word "Protect" slipped through, forcing Zane's systems to call up what had been defragmented.) -As a final act of spite for being broken, the Staff encoded Zane's memories of the Never realm to his Core Processing systems, meaning he cannot forget the Never Realm without completely frying his systems and rendering him a lifeless shell. (It might've also made a backup of itself amidst his various repressed memory files, but he doesn't need to know that. It's just sitting there, disguised as a normal .zip file, biding its time.) (I really like genre-blending Sci-Fi and Fantasy, and I thought the idea of "Magic Ice Computer Network" is rad as hell.)
(This song is a big part the inspiration for part of the "Dark Ice Network" idea, by the way. Granted, the Staff of Forbidden Spinjitzu doesn't assimilate Zane's psyche like Star Dream assimilates Haltmann's, but a lot of the ideas are still there-and the Staff does still integrate itself pretty deeply into the Nindroid's code as it slowly actualizes.)

I have no words for how absolutely awesome this is in every way. i just keep rereading this and being amazed. the "Dark Ice Network" idea is literally so cool, I particularly love the Ice Emperor being able to monitor the entire land while his body/the staff is the main 'hub' he has to protect. this is aweosme.
everyone look now please
#ninjago#zane julien#ns11#ninjago ice chapter#ninjago ice emperor#spinchip posts#<just so i can find it later
211 notes
·
View notes
Text
Tim doesn’t have a lot from Dana.
Two years of memories.
Just six or so months between her wedding to his father and Jack’s death. Another few months after that until Bludhaven exploded.
Two Christmases, and two birthdays.
The first Christmas never really happened as his dad and Dana were snowed in in Chicago. They’d come home bearing apology gifts, but Dana still didn’t really know Tim at that point, so it had been…stuff. New video games. A new watch. A new Discman. (Dad had ponied up for Green Day VIP tour tickets, out of guilt; Tim had taken Ives with him).
Tim had spent his fifteenth birthday in No Man’s Land. His present had been the government-funded extraction (which he had subsequently ignored only to sneak back in repeatedly).
That year, Tim had spent Christmas Eve in Bristol with his father, just the two of them. It was Jack’s concession to having missed the previous two Christmas Eves, between his coma and the previous year. (It had been two years since Tim had buried his mom. They’d visited the cemetery earlier that day, before Tim answered an urgent call from Oracle to go look for the babies kidnapped by the Joker).
For his sixteenth birthday, Bruce had given Tim a paranoid breakdown, his dad had given him a new wireless modem, and Dana had given him dress shoes.
For all his scepticism at the time, the shoes had eventually come in handy.
For the funerals.
Between the Crisis and the cruise and the chaos surrounding identifying bodies in Bludhaven, the Winters’ had handled Dana’s funeral. An invite hadn’t made it to Tim in time – he’d only met Dana’s family that once, at the wedding – but Alfred had seen the funeral notice in the paper and forwarded it to Tim.
Dana was buried outside of Gotham, with her grandparents. Bruce had taken Tim up to see the grave.
Two years, and a pair of shoes, and a recipe for soup. The memories of her laughter at the dinner table. A mug that she’d picked out and drank her coffee from every morning.
The silent gap of a third missing parent, one that people forget he ever had, because she was only his step-mother.
Little things.
#tim drake#dana winters#my fic#reasonably canonical - DC has more than one Christmas per year#so I took Holiday Bash III not I as Dana is mentioned in it
493 notes
·
View notes
Text
No More Lag: Get Best WiFi Routers in Australia
The world is highly connected. Online learning, remote work, smart homes including streaming have a reliable internet connection. However, an amazing experience doesn't have relevance to the service provider. Instead, it is dependent on wireless modems in Australia. No matter whether I want to choose the best wifi router in Australia or just want to upgrade to a newer one. Going ahead, we will walk you through everything related to Wifi Routers in Australia.
Understanding the Difference Between WiFi Modem and WiFi Router:

Modem: Makes the connection of your home to the internet via ISP i.e. Internet Service Provider. It further translates the signals from the ISP into a device form for easy usage.
Routers: Either Ethernet Cables or Wirelessly the router distributes internet connection from modem to different multiple devices.
If having a combo, then one gets both of the functionalities together into one device. Choosing this combo, one gets simplicity and convenience.
Why Investing in a Best Modem Router in Australia is Worthy?
In Australia, there are a vast type of ranges available including - NBN, ADSL, and cable. It is important to have an accurate router/modem which helps in unlocking the full potential of the internet.
Improved Coverage: No more dead zones in your office or home.
High Speed: With a good router you get to improve the internet speed.
Device Handling: The modern routers have the potential to handle different devices simultaneously.
Security: The advanced level of routers have in-built firewalls and automatic firmware updates.

Setup of Wireless Network Matters!
Having the best modem router in Australia is of full use only when the router is placed in a central location. You must avoid the thick furniture or walls between devices or routers. The firmware must be updated on a continuous basis for great performance and security. Moreover, a strong WiFi password must be used as the default admin credentials.
Source : https://theubntshop.blogspot.com/2025/04/power-your-network-with-ubnt-in.html
#Wireless Modems Australia#Wifi Routers Australia#Best Wifi Router Australia#Best Modem Router Australia
0 notes
Text
Prolifically waiting for ai to confuse diagnostic with diagnosis on a regular basis to itself as well as us. Like... I put my symptoms in and it tells me to unplug myself. I try to run the computer diagnostic and it tells me my modem has brain cancer; I need to check my brain interface and its positive it's wireless connectivity problems are a bloodflow issue.
59 notes
·
View notes
Text
Secure Connection
As promised: more Posie!! I wrote this one toward the end of last Spring after a couple of conversations with friends regarding the malleability of digital bodies (as well as still having Many Thoughts about the way code can give them new compulsions, after writing something about Annie and a new taur-shaped chassis for a friend's Patreon). Enjoy reading about her dealing with a corporate-mandated "hardware" update!
CW: Genital TF, this is another one that's As About Sex as it can possibly be without being about sex
Posie sat, sulking—steaming, even—in her office. It was a small side room off of the main floor of IT personnel, system engineers, and other technical employees of her corporation. Much like a central server, it was placed for easy access to the department-wide administrative assistant, and much like a server room, it was snug, windowless, and awash with the calming drone and relaxing warmth of an array of exhaust fans. Though she was free to project herself nearly anywhere on the company’s campus, this was where her consciousness was housed, and where she felt most at home. It was also the only place she could get any damn privacy, a luxury that she was deeply grateful for at present.
A newly-downloaded file weighed on the back of the Renamon’s mind. More literally, it was somewhere in the racks of drives that made up her long-term memory, to and from which mission-critical information was transferred in the course of doing business. Had somebody asked where exactly the file was stored, she would have been able to list the specific drive and the exact directory address, but she had de-prioritized the allocation of her processing resources for the download. Once again, she had received an assignment from her superiors, and once again, she was hesitant. She may even have admitted to being recalcitrant. She resented the orders.
The package of data in question was an update for her own software, a suite of new tools to allow management to offload yet more menial tasks onto her in the name of “efficiency”. Forget that she could diagnose a software issue faster than any of the engineers could even open a remote connection to the malfunctioning device. Instead of allowing her to take the reins, they saw fit to divert more of her attention to the least impressive among talents, and the one she already put to use the most often: transferring data.
This wouldn’t have been much of a problem, ordinarily. After all, Posie resided in the beating heart of the network, the nexus through which the vast majority of information was sent and received. It could be… meditative. Parsing streams of ones and zeroes, overseeing the flow of packets, redirecting traffic to equally spread the load across modems and routers so as to optimize travel time. It could even have been considered relaxing, if a worker of her caliber needed to relax. Instead of offering her a vacation (pah!), however, the update felt more like it heralded a demotion, denying her even the ability to pluck like harpstrings the miles of copper and gold that lined her facility. She was expected to deliver this data on foot.
Management justified this humiliation with practical concerns: some information, much like the old records she was often tasked to dispose of, was so confidential that it could not be sent via wireless transmission. Even hardwired connections were too fallible for the likes of next-generation schematics and financial access keys—a single compromised workstation, or compromised worker, could spell the loss of the company’s upper hand in its market. She wasn’t even going to be afforded the dignity of carrying an external hard drive to the destination. That would require the slow and tedious process of physically moving from one place to the next; this was one of the only times that she regretted the freedom of movement that was so coveted by her flesh-and-blood peers.
With no room to make exceptions for security protocol, she gripped the edge of her desk, brow furrowing, eyes squinted shut in consternation. Eventually, she huffed, rose, and turned her attention to her “physical body”, summoning up the file in much the same way that one would approach a plate of food with a pungent odor. The Renamon steeled herself and began to more closely examine its contents. She read the raw code similarly to how one might read words on a page; however, where the turning gears of the organic mind would, almost unconsciously, conjure up an image as a result of those words, her mind kicked off a series of involuntary, autonomic processes.
Her body carried out the instructions on her behalf. Once she started, she had no control until she finally reached a stopcode; it was the nature of being a program herself that code had as much of an influence on her mind and body as her own thoughts, her own will. In opening the package, she reluctantly consented to the changes that management saw fit to make to her. It was better than the eventual forced-deadline sort of update that software companies were so keen on using nowadays, and at least choosing the time and place allowed her to make herself presentable again before having to face another person.
Having parts of her code—her very body—rewritten by the update was a strange sensation, not unlike having your thoughts dictated to you by an outside force. Stranger still was that she could feel the exact delineation between her previous self and the patches of… well, the patch. She could feel it quite strongly, as a matter of fact: beneath her skirt of simulated sky-blue fur, between her legs, she could feel her mesh being edited. Stretched. Reshaped. The vectors that made up the triangles of her wireframe soul were being rewritten, mathematically transformed. A shape began to protrude from the once-flat span at the bottom of her torso, at first round and indistinct, but quickly increasing in resolution.
The Renamon struggled to process the sensations as a long, slender connector began to take shape. This often happened with changes to her body plan; inputs streamed into her mind from directions, locations, that previously never sent any signals, and the new additions seldom had their sensitivity adjusted downward for her convenience. In this case, it was highly sensitive, delivering reams of data to the base of her skull just from brushing up against her own fur, or the gentle flow of air from the computers in her office. It made sense, given that it was supposed to be a high-capacity transfer tool, but she was too busy buckling at the knees and clutching at the desk behind her so she didn’t fall flat on her rear for the thought to occur to her.
Her processors demanded more cooling, kicking into high gear as they formatted the two new storage devices that accompanied the connector, tailor-made for packing confidential data as tightly as possible. The sound of whirring fans filled the room, stirring her fur and sending shivers up and down her back; she could only hope that the rushing exhaust made enough noise to drown her out, whimpering despite herself. The new drives were larger (and more unwieldy) than the ones that were built into her chest, much to her chagrin. She was forced to adjust her stance and her gait as she found her footing again, spreading her legs wider than she was accustomed in order to give them enough room.
The spinning in her head slowly settling down, she slowly began to compose herself once again, taking stock of the new additions. They were cumbersome, to be sure, and she lamented how they jutted out from her otherwise sleek form and burdened her with less-graceful posture. It didn’t even match her fur! The software engineers that had concocted the code had at least included one small mercy: a compartment for the connector to retract into, nestled in the fur above the storage drives. No such luck for the drives themselves. She supposed she would just have to adjust to walking with delicate hardware in tow. As she went to smooth her fur over her lap again, her paw recoiled away. Some kind of… static discharge was left in the fluff. A memory leak, perhaps? The fact that such a malfunction could be caused just from having the connector brush up against her fur appalled her, deepening her frustration even more. They couldn’t even test the update for bugs before shipping it out to her. She shook out her paw and finished arranging her skirt as best she could before working up the composure to finally leave her office.
Picking up the payload for which all this fanfare had been arranged was at least a quick, easy process. She stopped into the office of the manager that had assigned her the task; she offered a businesslike nod and, knowing that she was always itching to skip niceties in the name of saving time, he offered a straightforward wave at his personal terminal. She held a paw over the computer tower and, in the time it took for electricity to arc to her fingertip with a tinny zzzrt, she had already searched his directory for the relevant test files and copied them to the newly-installed drives. Wireless transfer, yes, but only technically. The engineers had specifically asked a member of another division, whose computer network wasn’t connected to their own; it was as though she had picked a folder up from his desk and walked out with it.
Moving the file was just as uneventful. It was far from the first time that she’d navigated the sprawling corporate property, and even if it were, the maps existed just outside the orbit of her thoughts, ready to be summoned to mind at a simple impulse. What she was not expecting, however, was the technician who was waiting in the server room to which she was asked to deliver the file. While she preferred to work in the isolation of rooms that were set aside specifically for hardware, she was far from unused to being in the presence of the other people responsible for maintaining the company’s systems. That said…
“Can I help you?” The Renamon icily asked.
“Oh, I don’t need anything! I’m just here to take notes on the transfer.” Her tone was cheery; evidently, she wasn’t aware how compromising the new additions were. “The time it takes, any obvious issues. I’ll be the one checking the files against the originals, too,” she concluded, hooking a thumb over her shoulder at a monitor behind her.
“I see,” Posie replied through gritted teeth. “You have clearance to see these files, then?”
“Well, they’re just dummy data, ma’am.” At least she was respectful.
“And the proprietary hardware I’ve been… equipped with?” she forced out, keeping her synthesized voice even.
“Oh, for sure I do. I designed it!”
Oh! she seethed. So she knows pre-cise-ly the position he’s put me in.
“Well. I suppose there’s no point in delaying things, then.”
“Ready when you are!”
With tense shoulders, she turned toward the server rack, eyes darting over it, searching for where exactly she was supposed to connect to the array. After glancing over the contents of each drive, she found the one she was supposed to copy the data into—deposit would be more apt, as it was her understanding that the files would be automatically flushed from her system—and found a port that would allow her to access it. Conveniently, it was around waist height. She wondered, crossly, whether that had been an intentional design decision by this engineer as well. As she looked at it, she felt a twinge from the connector; on its own, like a Bluetooth device automatically searching for signals, it slid itself out from its fuzzy little compartment.
Her skin was abuzz, and her fur stood on end. She couldn’t quite tell if it was coming from the connector itself, or if it was the feeling of the programmer’s eyes on her If she could take a deep breath, she would have then. Without any way to stall further, or to tell the leering young woman to take her test files and store them somewhere indecent, she simply pushed forward with dropping off the damned data.
The instant the connector grazed the metal of the port, lightning shot into it, through her body, and into her head, making it swim with electrical potential. A stuttering, lagging thought made its way to the surface of her mind: they really had overtuned the sensitivity. She stifled a gasp and suppressed the urge to lay into the engineer (electrons were eager to flow out of her even without proper alignment with the contacts in the port, and didn’t she know that discharge like that could damage a piece of hardware?!), willing her body to keep pressing the stupid connector into the socket.
Even as she tried to get it over with already, something in the back of her mind compelled her to draw back a bit. If she had been restraining herself from reprimanding the engineer for risking the hardware, then she should at least do it the service of ensuring she was properly aligned, shouldn’t she? She obliged the impulse, and the motion all at once became much jerkier, less controlled. The friction of the port against her connector was enough to send her tail snapping back and forth, and she could tell that the temperature in her own server’s room had risen by a fair few degrees. Back and forth, wiggling side to side, she continued to readjust and realign herself, driven by unfamiliar code and overwhelmed by the signals pouring into her. She lost herself in the task, forgetting herself, forgetting her surroundings, until finally the technician cleared her throat.
“Ma’am,” she ventured, blushing and wide-eyed. “What, um. What are you doing? You should just need to plug it in.”
“I’m.” Her interruption had snapped the Renamon back to reality. She was mortified, tail sticking straight out and back ramrod straight. Her cheeks burned mercilessly. “I’m calibrating the connection.”
“Calibrating?”
“Did you want your files transferred with or without corrupted and incomplete data?” She snapped, hoping that her authoritative tone would head off any debate. “Assign me experimental hardware and then ask me to be reckless with it, hm? Should I be taking notes to give to our superiors?”
“I—alright, I guess you can’t be too careful,” she stammered, sheepishly pressing her legs together. “That was even something I tried to work into the design, so, c-carry on?”
“Thank you,” Posie blustered, turning back to the server rack. She did so slowly, reluctantly relishing the feeling of sliding around within the socket. She allowed herself one or two more “practice” attempts, hoping that it wouldn’t arouse too much suspicion from the engineer. Ultimately, just like before, there was no use in continuing to stall, and when she was able to bring her body to a stop, the rational part of herself was eager to be done with this entire torrid affair.
With more force, she pressed the connector inward one final time, trembling as the latch began to press against the opening. Slowly, agonizingly slowly, she continued, overwhelmed by the volume of electricity surging into her. The latch gave, compressing as it continued to slide inside, until finally it clicked into place, securing her to the array of drives and finalizing the connection.
All at once, a torrent of data poured out of her, an electron tsunami that felt like it threatened to spill out of the socket in which she was hilted. More data was transferred in the span of a few seconds than she was used to consciously processing, having cultivated such skill in delegating and compartmentalizing with background processes. Once again, the world around her was utterly drowned out; the strength fled her legs, and she clung to the steel bar that reinforced the top of the server rack, threatening to topple the entire system. Her self-control abandoned her as well and, forgetting the engineer, she cried out with an airy, wild, distinctly foxlike yelp. She screamed in surprise, gasped at the deluge of information, moaned because there was no room left in her mind for thought to do anything else.
Quickly, the disks of the server rack had finished writing the files she had carried to them, and her own drives were thoroughly purged. In another building, the radiators serving her processors shed heat at their absolute limits, and fans worked overtime to bring her back within her safe operational range. As her overworked circuitry began to chug through the backlog of sensory information, the entire experience caught up with her—including the detail that this entire shameless display had been carried out in front of that underhanded little engineer. She blinked, hard, and whipped her head to face her. For as hot as her own ears felt, the young woman’s face appeared to be glowing even brighter.
“What. Was that.”
“Um—”
“I’m used to new adjustments requiring desensitization, or even adjustment on their gain,” she growled, voice low and eerily even. “But that was a bridge too far to just have been miscalibration. Why did you design it like that?”
“Well, y-you remember how I mentioned, um, having considered an early disconnection?” Posie’s frosty glare didn’t waver, so the tech continued, answering her own rhetorical question. “That was, uh, the safeguard. Against early disconnection. I, figured it’d just be easier to make it so you wouldn’t want to unplug—”
“Do you think you have the au-thor-ity to go making changes to my mind, young lady?!”
“I-I can roll back the update if you want—”
“I think you’ve done QUITE enough!” The Renamon declared, despite herself. Perhaps it was genuine distrust, or perhaps—perhaps she truly couldn’t tell which desires were her own, at the moment. This would require careful study of her own system files.
Another small click broke the silence following her outburst, and the dongle began to retract from the server’s port and back into Posie’s body. Now free to move around, she dusted and fluffed her skirt and leaned down to look the engineer in the eye.
“I trust that you can report to your supervisor that I performed to your expectations,” she hissed. “And that there will be no need for any further discussion of your little project.” The programmer nodded, eyes even wider than before—and cheeks even redder? The Renamon scoffed, sneered, and spun, storming out the door, already allotting time in her schedule for the next time that she would be called upon for such a delivery.
Utterly unsurprisingly, she had been correct in her assessment that her superiors would take every opportunity to save their organic employees’ time at her expense. Confidential deliveries became a regular part of her routine, and though she had great disdain for being reduced to a mere courier for so much of the workday, she insisted upon completing the task to her usual, lofty standards.
Posie was as prompt as she always was, dropping everything to ferry information between privileged parties, striving to reduce latency even in more analogue forms of communication. There was the occasional complaint about how long downloads took once she had finally arrived at her location, but she was quick to remind such impatient recipients that the decision to follow this protocol came from on-high, and that even for someone who worked as quickly as her, great care for the safety of the data was a corner that simply could not be cut in the name of rushing around.
She was as meticulous about ensuring proper alignment with the port, fine-tuning her contact with the wires within, as the first time she had experimented with the new tools, and complaints about noise from the server room were easily dismissed as the usual stress of supporting her formidable computational power. After all, she was often venturing out of the range of her home network, hosting herself entirely on the recipients’ systems; was she at fault when they couldn’t handle the information throughput they asked of her?
Once the deliveries had become more routine, and none of her peers bothered to check in when they felt it was taking too long or getting too noisy, she began to find enjoyment in the solitude of her work, just as with the other, admittedly more tedious, tasks she was expected to carry out. With fewer prying eyes to judge her performance, she could make herself more comfortable while handling transfers. She didn’t have to worry that anybody would walk in on her in the debased state she often found herself in while connected directly to a data center, leaning her full weight on the poor rack, tongue lolling out and chest heaving air to keep her cool.
Then again, if somebody—especially that little technician who’d saddled her with these “upgrades”—wanted to question her efficacy, that was more than fine by her. Posie was a woman who prided herself in her work, and would seldom turn down a chance to demonstrate her first-rate hardware and unparalleled optimization. She would be more than happy to demonstrate just how quickly she could pump out information, and just how much throughput she was capable of.
Thank you for reading! If you want to see more of my work, you can check it out here and here!
#writeblr#trans author#furry fiction#renamon#tf#transformation#office lady#OL#cock growth#penis growth#indie author#mrow oc: posie#my writing#short story
23 notes
·
View notes
Text
As the Trump administration's Department of Government Efficiency (DOGE) continues to rampage through the United States federal government, essentially guided by Elon Musk, the group has also been upending traditional IT boundaries—evaluating digital systems and allegedly accessing personally identifiable information as well as data that has typically been off-limits to those without specific training. Last week, The New York Times reported that the White House is adding Musk-owned SpaceX’s Starlink Wi-Fi “to improve Wi-Fi connectivity on the complex,” according to a statement from White House press secretary Karoline Leavitt. The White House's Starlink internet service is reportedly being donated by the company.
Spotty internet is an annoying but highly solvable problem that WIRED has reported on extensively. Of course, the White House is a highly complex organization operating out of a historic building, but network security researchers, government contractors, and former intelligence analysts with years of experience in US federal government security all tell WIRED that adding Starlink Wi-Fi in a seemingly rushed and haphazard way is an inefficient and counterproductive approach to solving connectivity issues. And they emphasized that it could set problematic precedents across the US government: that new pieces of technology can simply be layered into an environment at will without adequate oversight and monitoring.
“This is shadow IT, creating a network to bypass existing controls,” alleges Nicholas Weaver, a member of the nonprofit International Computer Science Institute's network security team and a computer science lecturer at UC Davis. He adds that while secret and top secret information is typically (but not always) processed only on special, separate federal networks that have no wireless access, the security and uniformity of White House Wi-Fi is still extremely important to national security. “A network like the White House unclassified side is still going to be very sensitive,” he says.
“Just like the Biden Administration did on numerous occasions, the White House is working to improve WiFi connectivity on the complex,” White House spokesperson Karoline Leavitt tells WIRED in a statement.
A White House source who asked not to be named supported the switch, arguing that in some areas of the campus, “the old Wi-Fi was trash.”
Researchers point out that while Starlink is a robust commercial ISP like any other, it is not clear that it is being implemented in compliance with White House Communication Agency requirements. If the controls on the White House Starlink Wi-Fi are more lax than on other White House Wi-Fi, it could introduce security exposures and blind spots in network monitoring for anomalous activity.
“The only reason they'd need Starlink would be to bypass existing security controls that are in place from WHCA,” claims former NSA hacker Jake Williams. “The biggest issues would be: First, if they don't have full monitoring of the Starlink connection. And second, if it allows remote management tools, so they could get remote access back into the White House networks. Obviously anyone could abuse that access.”
One baffling aspect of the arrangement is that Starlink and other satellite internet is designed to be used in places that have little or no access to terrestrial internet service—in other words, places where there are no reliable fiber lines or no wired infrastructure at all. Instead of a traditional ISP modem, Starlink customers get special panels that they install on a roof or other outdoor place to receive connectivity from orbiting satellites. The New York Times reported, though, that the White House Starlink panels are actually installed miles away at a White House data center that is routing the connectivity over existing fiber lines. Multiple sources emphasized to WIRED that this setup is bizarre.
“It is extra stupid to go satellite to fiber to actual site,” ICSI's Weaver says. “Starlink is inferior service anyplace where you have wire-line internet already available and, even in places which don't, inferior if you have reasonable line of sight to a cell tower.”
Weaver and others note that Starlink is a robust product and isn't inherently unreliable just because it is delivered via satellite. But in a location where fiber lines are highly available and, ultimately, the service is being delivered via those lines anyway, the setup is deeply inefficient.
While Starlink as a service is technically reliable, incorporating it in the White House could create a long-term federal dependence on an Elon Musk–controlled service, which could create future instabilities. After European officials raised concerns earlier this month on whether Starlink might stop serving Ukraine, Musk posted on social media: “To be extremely clear, no matter how much I disagree with the Ukraine policy, Starlink will never turn off its terminals … We would never do such a thing or use it as a bargaining chip.”
16 notes
·
View notes
Text

🇺🇸 🚨
UNITED STATES CONGRESS PASSES SERIES OF ANTI-DEMOCRATIC AND PRO-WAR BILLS DESPITE PUBLIC OPPOSITION
The United States Congress and Senate passed a series of bills, including three controversial anti-democratic and pro-war bills, two of which were tied together, on Saturday, bypassing public opinion and popular opposition to the profligate, pro-war, globalist, Neolib/Neocon agenda currently driving United States domestic and foreign policy.
Included in the bills passed was a bill to force TikTok to divest from its connections with China at risk of being banned immediately, which naturally was tied to a Foreign aid bill.
However, as even Republican Senator Rand Paul mentioned in an opinion piece in Reason Magazine, the Bill is almost certain to lead to more power for American political elites and their administrations to pressure companies like Apple and Google to further ban apps and sites that offer contradictory opinions to that of the invented narratives of the American Political class.
Before long, Americans, many of whom are already poorly informed, and heavily misinformed by their mainstream media, could lose access to critical information that contradicts the narratives of the United States government and corporate elites.
Horrifically, this only the start. The US Congress also extended the newly revised FISA spy laws, which gives the United States government the power to spy on the electronic communications of foreigners, while also conveniently sweeping up the conversations of millions of Americans, as we learned years ago thanks to the sacrifices of whistle blowers and journalists like Edward Snowden, Chelsea Manning and Julian Assange.
The new FISA Law goes further than this, however, granting US Intelligence agencies the power to spy on the wireless communications of Americans in completely new ways.
A recent Jacobin article describes these new powers as a, "radical expansion of government surveillance that would be ripe for abuse by a future authoritarian leader", or it could just be used by the authoritarian leadership we have right now, and have had for decades.
In fact, when one commentator described the new powers as "Stasi-like," Edward Snowden himself replied with a long post in which he remarked, "invocation of "Stasi-like" is not only a fair characterization of Himes' amendment, it's probably generous. The Stasi dared not even dream of what the Himes amendment provides."
The amendment in question just "tweaks" the current law's definition of an "electronic communication provider," which is being changed to "any service provider," something extremely likely to be abused by the government to force anyone with a business, a modem and people using their broadband to collect the electronic communications of those people, while also forcing their victims into silence.
The government could essentially force Americans to spy on other people and remain silent about it. Cafe's, restaurants, hotels, business landlords, shared workspaces all could get swept up into the investigations of the Intelligence agencies.
Worse still, because picking out the communications of a single user would be next to impossible, all of their victim's data would end up being surrendered to the authorities.
Sadly, the assault on Americans by their own political elites didn't end there, to top this historic day in Congress, at time when the United States public debt is growing at an astounding rate of $1 trillion every 100 days, US lawmakers also passed a series of pro-war aid packages to American allies (vassals) totalling some $95 billion.
Included in the foreign aid bill are aid packages totalling $61 billion for the Ukraine scam, $26 billion for Israel's special genocide operation in the Gaza Strip, and $8 billion to the Indo-Pacific to provoke WWIII with China, at the same time we're also provoking a nuclear holocaust with the Russian Federation.
Also buried in these aid packages is the authorization for the United States government to outright steal the oversees investments of the Russian Federation, and thereby the Russian taxpayers.
Astonishingly, and in direct opposition to the wishes of their own voters, Republican support was won without the possibility of conditioning the aid to any kind of border security, this despite the issue being among the top biggest concerns of Republican voters.
Although much of the money is to be used replenishing the heavily depleted stocks of America's weapons and munitions, it remains unclear where the munitions are expected to come from, as US defense production has remained sluggish and slow to expand despite heavy investments and demand in recent years, despite the rapid urgency with which the policy elite describe the situation.
It bodes poorly for working Americans that only a relatively small handful of lawmakers opposed the bills, producing unlikely bedfellows like Senator Bernie Sanders and Senator Mike Lee in the Senate, opposing the FISA bill.
While in the House, the loudest opposition to the foreign aid bill mostly came from populist Republicans such as Marjorie Taylor Greene, Thomas Massie and Paul Goser. Only 58 Congresmembers voted against the Foreign Aid Bill in which the TikTok ban was tucked.
Not one word from American politicians about the need to raise the minimum wage, which hasn't been increased since 2009 despite considerable inflation, nor a word about America's endlessly growing homelessness crises, property crime increases, or the 40-year stagnation of American wages, the deterioration of infrastructure, and precious little was said besides complaints about border security over the immigration crises sparked by American Imperialist adventures and US sanctions.
What we've learned today is that we are highly unlikely to see any changes to the insane behavior of the US and its allies any time soon, neither with regards to the absolutely bonkers Neocon foreign policy leading us to the edge of abyss, nor the spending-for-the-rich/austerity-for-the-poor Neoliberal domestic policy of the last 45 years.
#source1
#source2
#source3
#source4
#source5
#source6
#source7
#source8
@WorkerSolidarityNews
Blue: titles are opinion pieces or analysis, and may or may not contain sources.
#us news#us politics#us domestic policy#us economic policy#us economy#us foreign policy#us foreign aid#foreign aid#ukraine#ukraine war#russo ukrainian war#russia ukraine war#israel#palestine#china#politics#news#geopolitics#world news#global news#international news#war#breaking news#current events#us imperialism#immigration crisis#fisa#fisa court#fisa bill#tiktok ban
53 notes
·
View notes
Note
*impression of modem*

searching…

…

YOU'RE TRYING TO IMITATE…A WIRELESS WIFI DEVICE?
#mcsm#mcsm episode 7#mcsm pama#ask blog#mcsm au#send asks#ask me anything#asks open#answered asks#ask#ofte!au#ofte!pama#order of the empires
8 notes
·
View notes
Text
The Versatility of an RF Transmitter Module in Modern Wireless Systems
Wireless communication has become an indispensable part of our daily lives, enabling devices to communicate seamlessly without the constraints of physical connections. At the heart of this wireless revolution lies an RF (Radio Frequency) transmitter module, a device that plays a pivotal role in ensuring efficient and reliable data transmission. In this article, we will explore the significance of an RF transmitter module, its functions, and its widespread applications.
Understanding an RF Transmitter Module
An RF transmitter module is an electronic device designed to transmit data wirelessly using radio waves. This module is a crucial component in various wireless communication systems, offering the ability to connect and exchange information between devices over varying distances.
Applications of an RF Transmitter Module
Remote Controls: An RF transmitter module is extensively used in remote control devices. This module enables the wireless operation of gadgets like TV remote controls, car key fobs, and garage door openers, making our lives more convenient.
Wireless Sensors: In industrial and IoT (Internet of Things) applications, an RF transmitter module facilitates the transmission of data from sensors to central hubs or servers. This is vital for real-time monitoring and data analysis.
Home Automation: Smart homes rely on an RF transmitter module to control lighting, thermostats, and security systems remotely. This enhances energy efficiency, security, and convenience for homeowners.
Wireless Alarms and Security Systems: An RF transmitter module is an integral component of home and industrial security systems. It transmits signals from various sensors, such as motion detectors and door/window sensors, to a central control unit, enabling prompt responses to security breaches.
How an RF Transmitter Module Works
An RF transmitter module takes electrical signals from a source, such as a sensor or microcontroller, and converts them into RF signals for wireless transmission. These RF signals are then transmitted via an antenna to the corresponding receiver module.
On the receiving end, an RF receiver module captures and demodulates these RF signals, converting them back into electrical signals for processing or display.
Advantages of RF Technology
Long Range: RF technology is known for its impressive range capabilities, making it suitable for applications that require communication over significant distances.
Reliability: RF communication is highly reliable, even in challenging environments with obstacles or interference.
Low Power Consumption: Many RF transmitter modules are designed for low power consumption, making them ideal for battery-operated devices.
Ease of Integration: An RF module is relatively easy to integrate into various electronic systems, thanks to standardized protocols and interfaces.
Conclusion
An RF transmitter module is the unsung hero of modern wireless communication. From the convenience of a TV remote to the complexity of IoT ecosystems, this module enables seamless data exchange across diverse applications. As technology continues to advance, RF modules will likely play an increasingly vital role in connecting the world around us. Whether it's sending a simple command or transmitting critical data, RF technology remains at the forefront of wireless communication.
For details, please click:https://www.nicerf.com/fsk-front-end-module/868mhz-rf-module-rf4463pro.html
Or click:https://www.alibaba.com/product-detail/RF4463PRO-OEM-915MHz-long-range-transceiver_60805516985.html?spm=a2747.manage.0.0.841c71d2mT3hkT
For consultation, please contact NiceRF (Email: [email protected])

0 notes